How can fix weak cookie attribute
How can fix weak cookie attribute in web.config?
The secure attribute is an option that can be set by the application server when sending a new cookie to the user within an HTTP Response. The purpose of the secure attribute is to prevent cookies from being observed by unauthorized parties due to the transmission of the cookie in clear text. After add secure attribute, the browser will prevent the transmission of a cookie over an unencrypted channel.
To remediate this vulnerability, we recommend setting the session ID cookie with the following attributes-
- Http-only: Prevents client-side scripts from accessing the cookie, reducing the likelihood of XSS attacks.
- Secure: Requires the cookie to be transmitted over a secure (HTTPS) connection, reducing the likelihood of man-in-the-middle attacks.
- Same-site: Restricts the cookie to be sent only to the same origin site, reducing the likelihood of CSRF attacks.
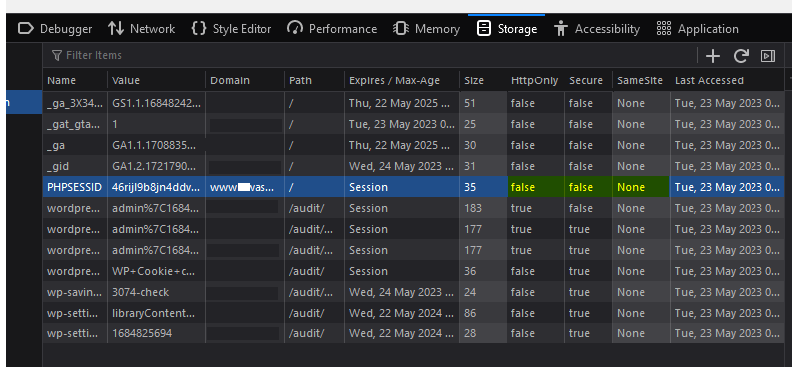
Security Impact:
This vulnerability exposes the session ID cookie to various attacks, such as session hijacking, cross-site scripting (XSS), and cross-site request forgery (CSRF). Attackers can steal the session ID cookie and use it to impersonate the user, allowing them to perform unauthorized actions on behalf of the user.
- You can fix weak cookie attribute by add bellow code in web.config file on server –
<system.web>
<httpCookies httpOnlyCookies="true" requireSSL="true" />
</system.web>
<system.webServer>
<outboundRules>
<clear />
<rule name="Use only secure cookies" preCondition="Unsecured cookie">
<match serverVariable="RESPONSE_SET_COOKIE" pattern=".*" negate="false" />
<action type="Rewrite" value="{R:0}; secure" />
</rule>
<preConditions>
<preCondition name="Unsecured cookie">
<add input="{RESPONSE_SET_COOKIE}" pattern="." />
<add input="{RESPONSE_SET_COOKIE}" pattern="; secure" negate="true" />
</preCondition>
</preConditions>
</outboundRules>
</system.webServer>- Add bellow code in header of a page to set a cookies values and status –
<?php
$rand= md5(rand());
header("Set-Cookie: PHPSESSID=$rand; httpOnly");
?>
good post sir